IT outsourcing opens the door to cost savings, expert support, and greater agility, but, it also opens windows to potential vulnerabilities. One wrong move and your business could become a statistic. As CloudSecureTech reports, data breaches cost businesses an average of $4.88 million per incident. That’s a steep price for a shortcut without a safety net.
| “Strategic IT outsourcing can unlock growth, but only when risks are proactively managed.” – Bradd Konert, President of Gamma Tech Services |
Let’s delve into the multifaceted benefits and potential pitfalls of IT outsourcing, and how to navigate them effectively.
Experience Proactive IT solutions
Gamma Tech Services delivers the reliable, scalable, and secure support your business deserves.
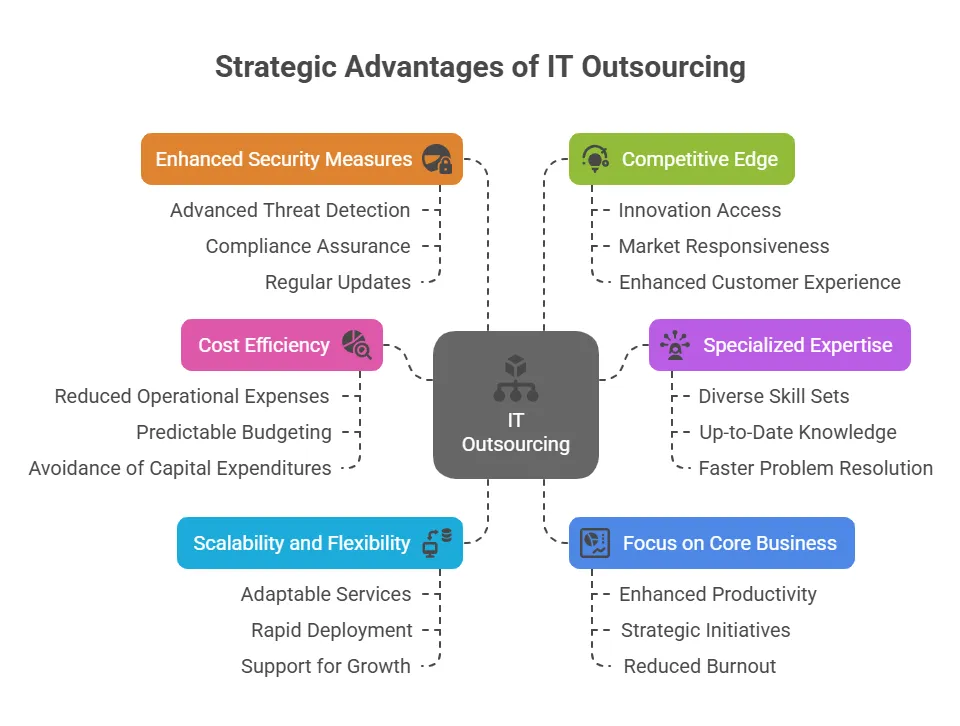
Get Started TodayThe Strategic Advantages of IT Outsourcing
1. Cost Efficiency
Outsourcing IT services can lead to significant cost savings by eliminating the need for in-house infrastructure and personnel. Businesses can convert fixed IT costs into variable ones, allowing for more effective budget planning.
Key Points:
- Reduced Operational Expenses: Outsourcing eliminates the need for significant investments in hardware, software, and personnel.
- Predictable Budgeting: Fixed monthly fees for outsourced services allow for more accurate financial planning.
- Avoidance of Capital Expenditures: Businesses ca avoid large upfront costs associated with setting up IT infrastructure.
2. Access to Specialized Expertise
By outsourcing, companies gain access to a global talent pool with specialized skills that may not be available internally. This includes expertise in areas like cybersecurity, cloud computing, and data analytics.
Key Points:
- Diverse Skill Sets: Outsourcing partners often have teams with a wide range of technical skills.
- Up-to-Date Knowledge: External experts stay current with the latest industry trends and technologies.
- Faster Problem Resolution: Specialized knowledge allows for quicker identification and resolution of issues.
3. Scalability and Flexibility
Outsourcing allows businesses to scale IT resources up or down based on demand, providing flexibility to adapt to changing market conditions.
Key Points:
- Adaptable Services: Easily adjust the level of services based on business needs.
- Rapid Deployment: Quickly implement new technologies or services without lengthy hiring processes.
- Support for Growth: Outsourcing partners can accommodate business expansion without significant delays.
4. Focus on Core Business
Delegating IT functions enables internal teams to concentrate on core business activities, enhancing overall productivity and strategic focus.
Key Points:
- Enhanced Productivity: Employees can focus on their primary roles without IT distractions.
- Strategic Initiatives: Management can allocate more time to business development and innovation.
- Reduced Burnout: Minimizing multitasking reduces employee stress and turnover.
5. Enhanced Security Measures
Specialized IT providers often have advanced security protocols in place, helping businesses bolster their cybersecurity posture.
Key Points:
- Advanced Threat Detection: Outsourcing partners use sophisticated tools to identify and mitigate threats.
- Compliance Assurance: Ensure adherence to industry regulations and standards.
- Regular Updates: Continuous monitoring and updating of security measures can help protect your IT from emerging threats.
6. Competitive Edge
Access to the latest technologies and innovations through outsourcing can provide businesses with a competitive advantage in their industry.
Key Points:
- Innovation Access: Stay ahead with cutting-edge technologies and practices.
- Market Responsiveness: Quickly adapt to market changes with flexible IT solutions.
- Enhanced Customer Experience: Implementing the latest tools can improve service delivery and customer satisfaction.
Navigating the Risks of IT Outsourcing
1. Data Security Concerns
Entrusting sensitive data to third-party providers introduces potential vulnerabilities. It’s crucial to ensure that outsourcing partners have robust security measures in place.
Key Points:
- Data Breaches: Unauthorized access to sensitive information can lead to significant financial and reputational damage.
- Compliance Risks: Failure to comply with data protection regulations can result in legal penalties.
- Mitigation Strategies: Implement strict access controls and regular security audits, and ensure partners adhere to compliance standards.
2. Loss of Control
Outsourcing can lead to a perceived or actual loss of control over certain business functions, making it essential to establish clear governance structures.
Key Points:
- Dependency: Over-reliance on external providers can limit internal decision-making.
- Quality Assurance: Ensuring consistent service quality requires effective oversight.
- Mitigation Strategies: Define clear roles and responsibilities, and maintain regular communication with providers.
3. Communication Barriers
Differences in time zones, language, and culture can impede effective communication, potentially affecting project outcomes.
Key Points:
- Misunderstandings: Language and cultural differences can lead to misinterpretations.
- Delayed Responses: Time zone differences may slow down communication and decision-making.
- Mitigation Strategies: Establish clear communication protocols, use collaborative tools, and schedule regular meetings.
| Learn More About How You Can Set Your IT Team Up For Success How to Choose Managed IT Services Provider Cord Cutting (Should you make this switch) How Much Storage Should I Have For My NVR? |
4. Quality Assurance
Ensuring consistent quality from external providers can be challenging, necessitating regular performance evaluations.
Key Points:
- Inconsistent Deliverables: Variability in service quality can affect business operations.
- Lack of Accountability: External providers may not align with internal quality standards.
- Mitigation Strategies: Implement Service Level Agreements (SLAs) and conduct regular performance reviews.
5. Hidden Costs
Unanticipated expenses, such as additional fees for services outside the initial agreement, can arise, emphasizing the need for detailed contracts.
Key Points:
- Unexpected Charges: Additional costs for extra services or changes in scope.
- Contractual Ambiguities: Vague terms can lead to misunderstandings and disputes.Mitigation Strategies: Ensure comprehensive contracts outline all potential costs and scenarios.
6. Dependency Risks
Over-reliance on a single outsourcing provider can pose risks if the provider fails to deliver or goes out of business.
Key Points:
- Service Disruptions: Provider issues can lead to operational downtime.
- Limited Flexibility: Dependence on one provider may hinder adaptability.
Benefits vs. Risks of IT Outsourcing
| Benefits | Risks |
| Cost Savings | Data Security Concerns |
| Access to Specialized Skills | Loss of Control |
| Scalability and Flexibility | Communication Barriers |
| Focus on Core Business | Quality Assurance Challenges |
| Enhanced Security Measures | Hidden Costs |
| Competitive Edge | Dependency on Providers |
Unlock the Full Potential of IT Outsourcing with Gamma Tech Services
Outsourcing your IT functions can be a game-changer, but only if approached with a clear strategy. When done right, it helps you cut costs, tap into top-tier expertise, scale fast, and stay focused on what your business does best. However, risks like data exposure, poor communication, and vendor lock-in can quickly turn opportunity into liability.
That’s where Gamma Tech Services comes in.
We don’t just provide IT services; we have become your trusted partner in digital transformation. As a leading managed services provider, Gamma Tech Services brings years of experience, proactive support, airtight security standards, and the agility to scale with your business.
Ready to take control of your IT? Book a consultation with Gamma Tech Services today and let’s turn smart outsourcing into strategic success.
| Choose From a Range of IT Services in Naples, Florida! | |
| IT Support Services Cybersecurity IT Network Support | IT Consulting IT Helpdesk IT Outsourcing |



